OSI Model Encapsulation
The OSI (Open Systems Interconnection) Model is a theoretical framework that defines how different networking protocols interact across various layers to enable
communication. It is useful for certifications like CCNA or certain Microsoft networking exams.
OSI Layers
Application Layer (Layer 7)
This layer provides services for end-user applications that use the network, such as FTP, HTTP, or your web browser.Presentation Layer (Layer 6)
The presentation layer translates data into a format that can be transmitted over the network. Examples include JPEG, ASCII, and XML.Session Layer (Layer 5)
Responsible for managing sessions between applications, such as keeping track of RPC (Remote Procedure Calls). Examples include SQL and Microsoft Exchange.Transport Layer (Layer 4)
Ensures reliable transmission of data. The most common transport protocol is TCP (Transmission Control Protocol), ensuring data arrives correctly.Network Layer (Layer 3)
Handles routing and addressing, using protocols like IP (Internet Protocol). Routers operate at this layer.Data Link Layer (Layer 2)
Transmits frames over the physical medium. Ethernet and PPP (Point-to-Point Protocol) are examples. Switches operate at this layer.Physical Layer (Layer 1)
Concerned with the physical hardware transmission, such as cables, hubs, and network interface cards.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
DNS (Domain Name System) Lookup
DNS translates human-readable domain names (e.g., www.example.com) into IP addresses. It is critical for network functionality, and if DNS fails, most network functions fail.
DNS Functions
Forward DNS Lookup: Translates domain names into IP addresses.
Reverse DNS Lookup: Translates IP addresses into domain names.
IPCONFIG Command: Using ipconfig /all in Windows displays the configured DNS servers.
How DNS Works
User enters a domain name.
The request goes to a DNS resolver, usually managed by the user's ISP.
The resolver contacts root and top-level domain (TLD) name servers.
It retrieves the authoritative name server for the domain.
The resolver fetches the IP address associated with the domain and returns it to the user's browser.
The web server at that IP address sends the requested content to the user.
Types of DNS Services
Authoritative DNS: Holds DNS records and responds to DNS queries with the necessary IP address.
Recursive DNS: Retrieves information on behalf of the user by querying authoritative servers.
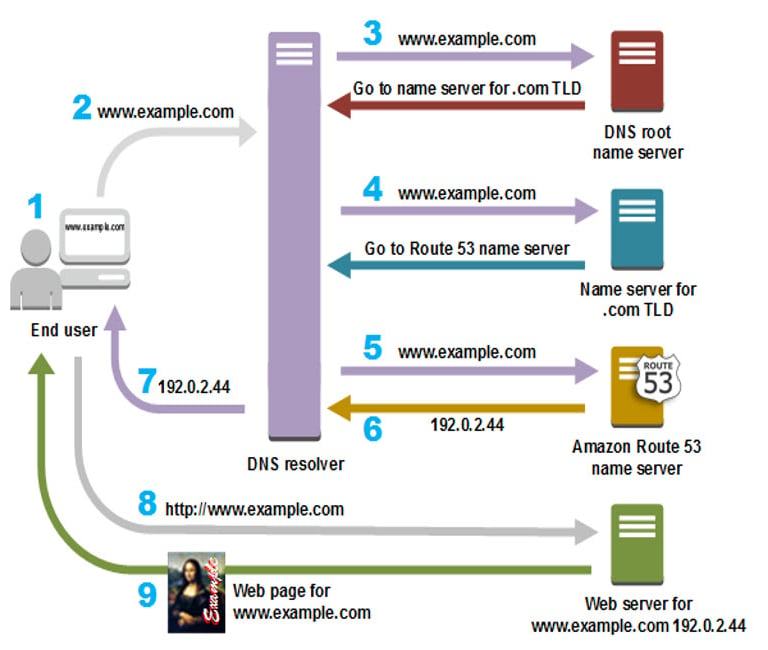
The following diagram gives an overview of how recursive and authoritative DNS services work together to route an end user to your website or application.
A user opens a web browser, enters www.example.com in the address bar, and presses Enter.
The request for www.example.com is routed to a DNS resolver, which is typically managed by the
user's Internet service provider (ISP), such as a cable Internet provider, a DSL broadband provider,
or a corporate network.The DNS resolver for the ISP forwards the request for www.example.com to a DNS root name server.
The DNS resolver for the ISP forwards the request for www.example.com again, this time to one of
the TLD name servers for .com domains. The name server for .com domains responds to the request
with the names of the four Amazon Route 53 name servers that are associated with the example.com
domain.The DNS resolver for the ISP chooses an Amazon Route 53 name server and forwards the request
for www.example.com to that name server.The Amazon Route 53 name server looks in the example.com hosted zone for the www.example.com
record, gets the associated value, such as the IP address for a web server, 192.0.2.44, and returns the
IP address to the DNS resolver.The DNS resolver for the ISP finally has the IP address that the user needs. The resolver returns that
value to the web browser. The DNS resolver also caches (stores) the IP address for example.com for
an amount of time that you specify so that it can respond more quickly the next time someone browser
to example.com. For more information, see time to live (TTL).The web browser sends a request for www.example.com to the IP address that it got from the DNS resolver. This is where your content is, for example, a web server running on an Amazon EC2 instance or an Amazon S3 bucket that's configured as a website endpoint.
The web server or other resource at 192.0.2.44 returns the web page for www.example.com to the web browser, and the web browser displays the page.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
IP Addressing
An IP address is a unique identifier assigned to each device connected to a network. IP addresses can be obtained manually or through DHCP (Dynamic Host Configuration Protocol).
Types of IP Addresses
IPv4: Uses a 32-bit address format (e.g., 192.168.1.1).
IPv6: Uses a 128-bit address format (e.g., 2001:0db8:85a3::0370:7334).
Public IPs: Assigned by ISPs for internet communication.
Private IPs: Used within local networks, not directly accessible from the internet.
Subnetting
Larger blocks of IP addresses can be divided into smaller subnets to efficiently allocate IPs across networks.
ARP (Address Resolution Protocol)
Maps IP addresses to MAC addresses, essential for device communication within a local network.
Class A
Range: 0.0.0.0 – 127.255.255.255
Default Subnet Mask: 255.0.0.0
Number of Hosts: Supports up to 16 million hosts.
Usage: Used for large networks like ISPs.
Class B
Range: 128.0.0.0 – 191.255.255.255
Default Subnet Mask: 255.255.0.0
Number of Hosts: Supports up to 65,000 hosts.
Usage: Medium-sized networks, universities, and large businesses.
Class C
Range: 192.0.0.0 – 223.255.255.255
Default Subnet Mask: 255.255.255.0
Number of Hosts: Supports up to 254 hosts.
Usage: Small networks and individual households.
Class D
Range: 224.0.0.0 – 239.255.255.255
Usage: Reserved for multicast groups (data sent to multiple destinations).
Class E
Range: 240.0.0.0 – 255.255.255.255
Usage: Reserved for research and development purposes.
Types of IP Addresses
Public IP Addresses: Assigned by ISPs for communication over the internet.
Private IP Addresses: Used within private networks, not routable over the internet.
Examples:
Class A Private Range: 10.0.0.0 – 10.255.255.255
Class B Private Range: 172.16.0.0 – 172.31.255.255
Class C Private Range: 192.168.0.0 – 192.168.255.255
IP routing: The process of directing data packets from a source device to a destination device across different networks. Here's how IP routing works:
Basic Principles
When a device sends data to another device on a different network, it passes the data to its default gateway (usually a router).
The router examines the destination IP address of the packet and consults its routing table to determine the best path to forward the packet.
The packet is then sent to the next router (hop) along the chosen path.
This process repeats at each router until the packet reaches its final destination.
Routing Tables
Routers maintain routing tables that contain:
Network destinations and subnet masks
Next-hop addresses or outgoing interfaces
Metrics (to determine the best path)
Routing tables can be populated through:
Directly connected networks
Static routing (manually configured)
Dynamic routing (using routing protocols)
Routing Protocols
Routing protocols help routers exchange information about network topologies and update their routing tables. Common routing protocols include:
RIP (Routing Information Protocol): Used in smaller networks, based on hop count.
OSPF (Open Shortest Path First): Used in larger networks, based on link-state algorithms.
BGP (Border Gateway Protocol): Used for internet routing between autonomous systems.
Routing Process
A device sends a packet to its default gateway (router).
The router checks its routing table for the best match to the destination IP address.
If a match is found, the router forwards the packet to the next-hop address or out the appropriate interface.
If no match is found, the router may use a default route or discard the packet.
This process continues at each router until the packet reaches its destination.
IP Forwarding Algorithm
The basic IP forwarding algorithm follows these steps:
Check if the destination IP matches a directly connected network.
If not, check the routing table for a matching route.
If a matching route is found, send the packet to the next-hop address.
If multiple matches exist, use the route with the longest subnet mask.
If no match is found, use the default route if available.
If no default route exists, send an error message to the source.
IP routing is crucial for the functioning of the internet and other IP-based networks, enabling efficient communication between devices across different networks
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
DHCP (Dynamic Host Configuration Protocol)
A DHCP server automatically assigns IP addresses, default gateways, and DNS server
information to client devices.
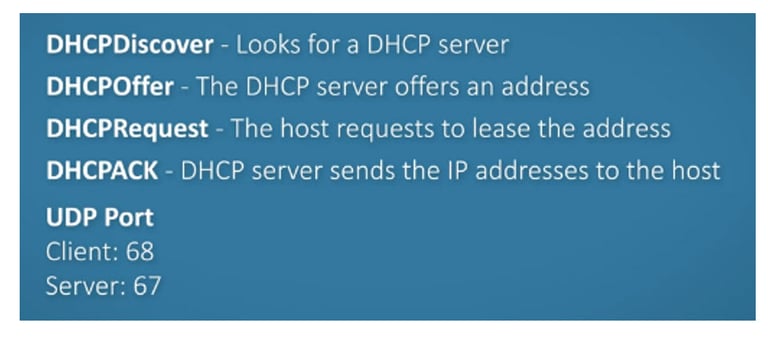
DHCP Workflow
Client requests an IP address (DHCP Discover).
Server offers an IP address (DHCP Offer).
Client accepts the offer (DHCP Request).
Server acknowledges the lease (DHCP Acknowledgement or DHCPACK).
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Routing and IP Forwarding
Routing is the process of forwarding data packets from one network to another. Routers use routing tables and protocols to determine the best path for data.
Routing Protocols
RIP (Routing Information Protocol): Based on hop count, used in smaller networks.
OSPF (Open Shortest Path First): A link-state protocol used in larger networks.
BGP (Border Gateway Protocol): The primary protocol for routing between autonomous systems on the internet.
IP Forwarding Algorithm
Check if the destination is a directly connected network.
Consult the routing table for the best match.
Forward the packet to the next hop based on the routing table.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
SAN (Storage Area Network) & NAS (Network Attached Storage)
SAN
Provides block-level storage access over a dedicated network, typically for high-performance, large-scale storage.
NAS
Offers file-level storage over a standard IP network, ideal for simpler setups.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Citrix and NetScaler
Citrix Workspace
Citrix provides remote desktop and application delivery services. Tools include
XenApp, XenDesktop, and StoreFront log viewer.
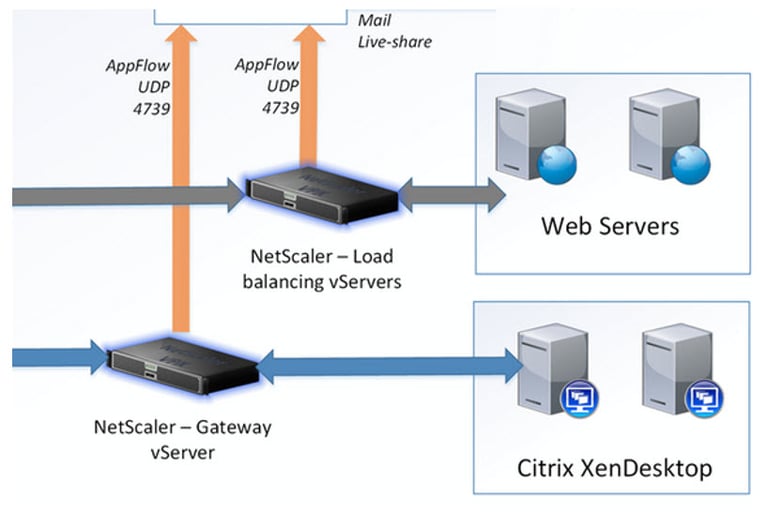
NetScaler
Citrix NetScaler handles SSL traffic offloading, acting as an liaison for secure
communications between clients and application servers.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
LDAP (Lightweight Directory Access Protocol)
LDAP is used for accessing and managing directory information services. It is an open standard based on the X.500 standard, typically used for storing user credentials and other directory information.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
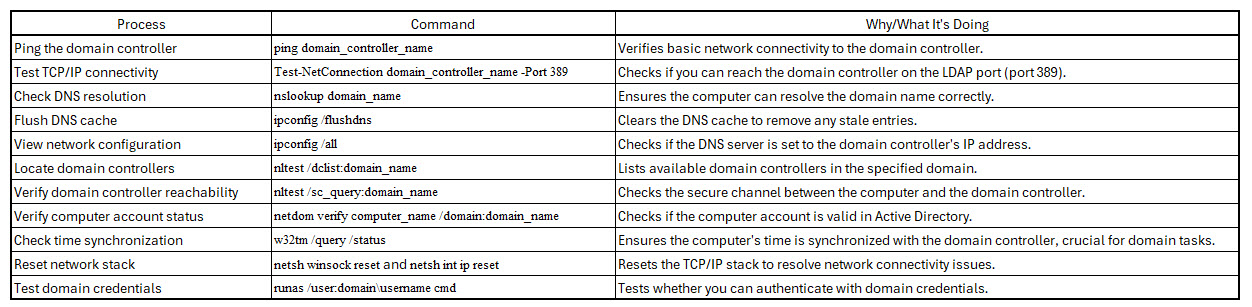
Network Troubleshooting Commands
Network Connectivity
ping domain_controller_name: Verifies basic network connectivity.
Test-NetConnection domain_controller_name -Port 389: Checks TCP/IP connectivity on the LDAP port.
DNS Tests
nslookup domain_name: Verifies DNS resolution.
ipconfig /flushdns: Clears DNS cache.
Active Directory and Domain Checks
nltest /dclist:domain_name: Lists domain controllers.
netdom verify computer_name /domain:domain_name: Verifies the computer's account in Active Directory
To troubleshoot why a computer won't connect to a company domain, you can use several command line tools. Here are some key commands and steps to diagnose the issue:
After running these commands, analyze the output for any errors or inconsistencies. If issues persist, you may need to:
- Reset the computer account in Active Directory
- Check for Group Policy issues
- Verify firewall settings
- Ensure the correct network drivers are installed
Remember to run these commands with administrative privileges. If the problem continues, you may need to rejoin the computer to the domain or seek assistance from your network administrator.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
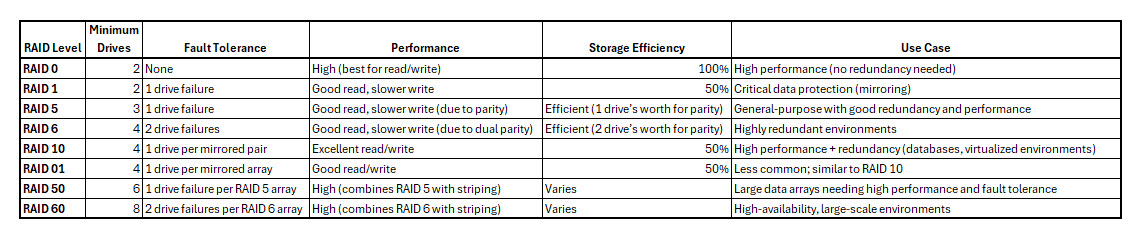
RAID
(Redundant Array of Independent Disks) is a technology that combines multiple physical hard drives into one or more logical units for the purpose of redundancy, performance improvement, or both. The data is distributed across these drives in various ways depending on the RAID level. Here are the most common types of RAID:
1. RAID 0 (Striping)
How it works: RAID 0 splits data into blocks and spreads it across multiple drives (striping), meaning that each drive holds part of the data.
Advantages:
Improved read and write performance because data is spread across multiple drives, allowing simultaneous access.
All storage space is used; there is no redundancy.
Disadvantages:
No redundancy. If one drive fails, all data is lost.
Use case: High-performance applications where data redundancy is not crucial (e.g., video editing, gaming).
2. RAID 1 (Mirroring)
How it works: RAID 1 duplicates the same data onto two or more drives (mirroring).
Advantages:
High redundancy. If one drive fails, the system can continue running with the other mirrored drive.
Read performance can be improved as data can be read from multiple disks.
Disadvantages:
Only half of the total drive capacity is usable because all data is duplicated.
Use case: Applications where data protection is important, such as databases, operating system disks, or small business servers.
3. RAID 5 (Striping with Parity)
How it works: RAID 5 stripes data across three or more drives and includes parity data for redundancy. The parity data is used to rebuild data in case of a drive failure.
Advantages:
Provides both performance and redundancy.
Can tolerate the failure of one drive without data loss.
Efficient use of storage: requires only one drive's worth of space for redundancy, regardless of how many drives are in the array.
Disadvantages:
Slower write speeds due to the overhead of calculating and writing parity data.
Can only tolerate one drive failure; if a second drive fails during rebuild, all data is lost.
Use case: Systems requiring a balance between performance, storage efficiency, and redundancy, such as file servers or web servers.
4. RAID 6 (Striping with Double Parity)
How it works: RAID 6 is similar to RAID 5 but uses double parity, allowing the system to survive the failure of two drives.
Advantages:
Higher redundancy than RAID 5 since it can tolerate two drive failures.
Good read performance, similar to RAID 5.
Disadvantages:
Slower write speeds compared to RAID 5 due to the need for two sets of parity data.
Requires at least four drives.
Use case: Systems where redundancy is critical and downtime due to data loss must be minimized, such as large file servers or storage-heavy applications.
5. RAID 10 (Mirroring + Striping)
How it works: RAID 10 (or RAID 1+0) combines RAID 1 and RAID 0. It stripes data across multiple mirrored pairs of drives.
Advantages:
Combines the redundancy of RAID 1 and the performance benefits of RAID 0.
High fault tolerance: even with one drive failure in each mirrored pair, the system can keep running.
Excellent read/write performance.
Disadvantages:
High cost, as half of the storage is used for mirroring.
Requires at least four drives.
Use case: High-performance systems that require both speed and redundancy, such as enterprise databases or virtualization environments.
6. RAID 01 (Striping + Mirroring)
How it works: RAID 01 (or RAID 0+1) is the opposite of RAID 10. It mirrors two RAID 0 arrays. Data is first striped, and then each stripe set is mirrored.
Advantages:
Provides both redundancy and performance, similar to RAID 10.
Disadvantages:
Lower fault tolerance than RAID 10. If one disk in a stripe set fails, the entire stripe set becomes inaccessible.
Use case: RAID 01 is rarely used because RAID 10 provides better fault tolerance.
7. RAID 50 (RAID 5 + Striping)
How it works: RAID 50 combines RAID 5 arrays with striping (RAID 0). Data is striped across multiple RAID 5 arrays.
Advantages:
Higher performance and redundancy than RAID 5 alone.
Can tolerate multiple drive failures, depending on the number of RAID 5 arrays.
Disadvantages:
More complex and requires a larger number of drives (minimum of six).
Expensive and can be challenging to manage.
Use case: Large-scale storage systems where performance and fault tolerance are critical, such as large databases and heavy-duty application servers.
8. RAID 60 (RAID 6 + Striping)
How it works: RAID 60 combines RAID 6 arrays with striping. Data is striped across multiple RAID 6 arrays.
Advantages:
Even greater fault tolerance than RAID 50 since RAID 6 can tolerate two drive failures in each array.
Suitable for environments where high redundancy and performance are required.
Disadvantages:
More complex and costly, requiring at least eight drives.
Write performance can be slower due to double parity calculations.
Use case: Mission-critical applications requiring very high fault tolerance and performance, such as large enterprise data centers
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Cybersecurity
Best practices focus on protecting systems, networks, and data. These include:
Regular Updates and Patch Management: Keep software and systems updated to mitigate vulnerabilities.
Strong Password Policies: Enforce complex passwords and use multi-factor authentication (MFA).
Firewalls and Anti-malware Solutions: Deploy robust firewalls and real-time malware protection.
Data Encryption: Encrypt sensitive data in transit and at rest.
User Training: Conduct regular cybersecurity awareness training.
Backup and Incident Response: Implement backups and an incident response plan for breaches or malware infections.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Other:
To answer the question "where do I see myself in 5 years"
In five years, I envision myself in a senior systems administrator or IT management role, leveraging my technical expertise and leadership skills to drive strategic IT initiatives. I aim to deepen my knowledge in cloud technologies and cybersecurity, while also mentoring junior staff and contributing to the overall efficiency and security of IT operations. I am excited to continue advancing within an organization that values innovation and professional development.
Questions:
Ask for a more detailed description of what they are looking for and the duties and responsibilities of the position.
Why is the position open?
Why isn’t Nashville listed on the website?
What’s the difference between Hawesville and Nashville locations?
What do you expect my first 30/60/90 days to look like?
What immediate challenges do you anticipate?
What are some of the short-term problems that need to be solved?
#1: What do the day-to-day responsibilities of the role look like?
#2: What are the company’s values? What characteristics do you look for in employees in order to represent those values?
#3: What’s your favorite part about working at the company?
#4: What does success look like in this position, and how do you measure it?
#5: Are there opportunities for professional development? If so, what do those look like?
#6: Who will I be working most closely with?
#7: Is there anything about my background or resume that makes you question whether I am a good fit for this role?
What is my weakness
One of my biggest challenges is occasionally over committing by taking on more tasks than I can realistically manage which leave me feeling a bit overwhelmed.
To address this, I’ve developed a habit of using a planner to track all my ongoing projects and tasks. It helps me get a clear sense of my workload, making it easier to determine whether I have the capacity for additional responsibilities. It’s also beneficial for keeping my manager in the loop, allowing us to prioritize key tasks together more effectively